Expected behaviour of Primary and Secondary Database Firewalls configured as a resilient pair
Resilient mode works in DAM mode only.
Both primary and secondary database firewalls:
- Receive the same span traffic
- Have the same configuration (the Management Server synchronizes this)
- Create log files according to the policy applied
- Sends out real-time alerts
- Runs user role and stored procedure audits
If the Primary database firewall is not available/cannot be contacted by the Management server, it collects the log files from the Secondary database firewall and promotes it to be Primary (so it will start sending out real-time alerts and running SPA/URA).
NOTE: The procedure described here applies to a Database Firewall in DAM mode only.
Prerequisites:
You cannot have Enforcement Points already created in Oracle Audit Vault otherwise you will get the following error:
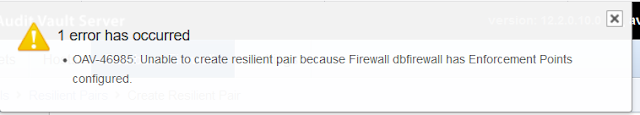
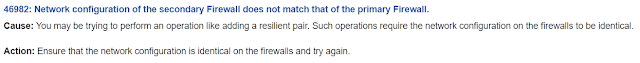
The IP of both Database Firewalls must be identical in the network configuration, otherwise you will receive the following error:
I recommend the following:
Configuring Oracle Database Firewalls as Resilient Pair

The IP of both Database Firewalls must be identical in the network configuration, otherwise you will receive the following error:

I recommend the following:
- In both Database Firewall go to:
- “System” -> “Network" And compare the following sections between both Oracle Database Firewall:
- Management Interface
- Traffic Sources
- Traffic Proxies
- Unallocated Network Interfaces
Configuring Oracle Database Firewalls as Resilient Pair
Click in “Database Firewall”
Click in “Resilient Pairs”
Click in “Create” Button
Select Primary and Secondary Database Firewalls
You will see that the Resilient Pair was added









No hay comentarios:
Publicar un comentario